Single login - Single Sign On: Log in. Just Once

Users of this system have no explicit or implicit expectation of privacy.
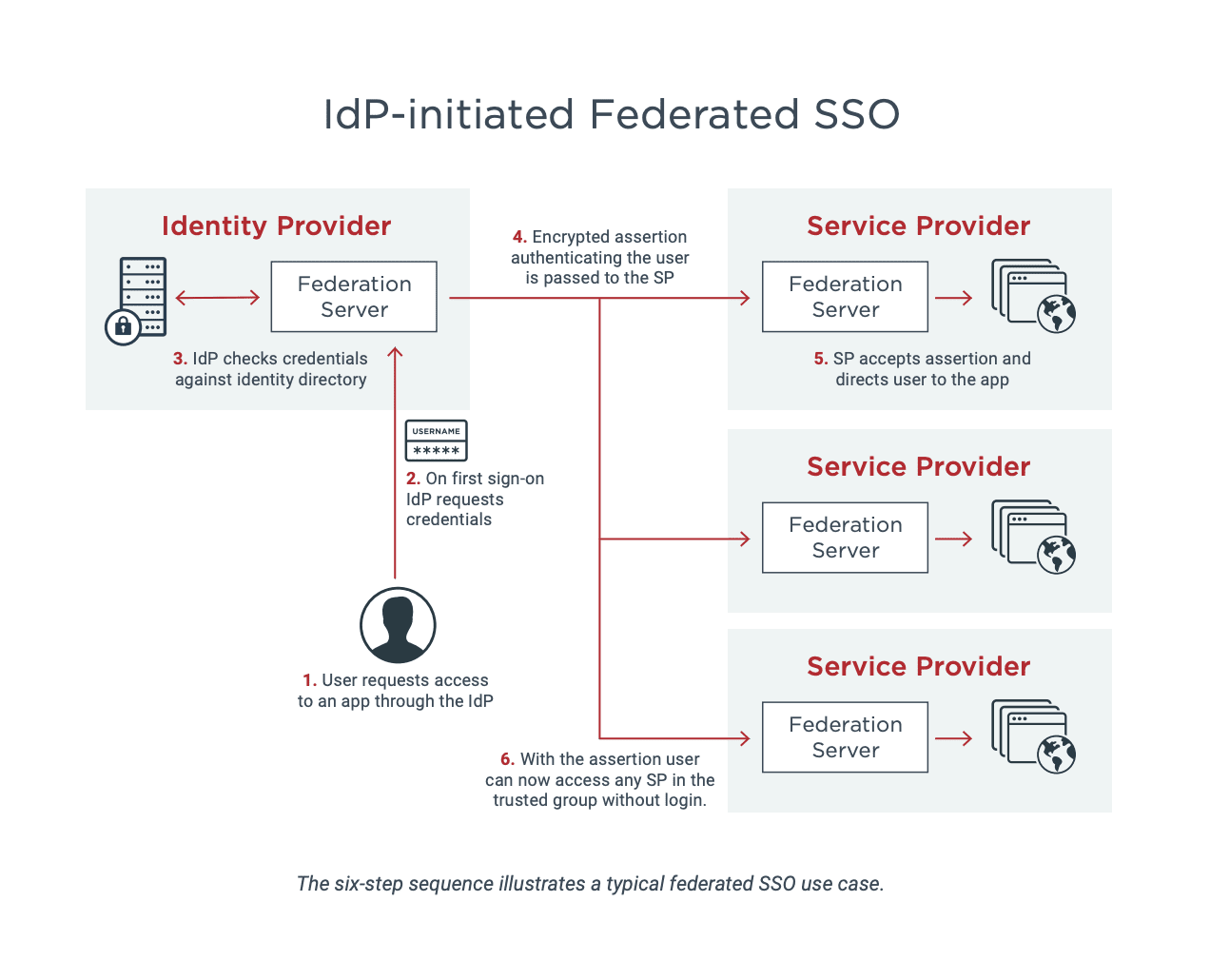
Users no longer have to keep track of different sets of credentials and can simply remember a single more complex password.


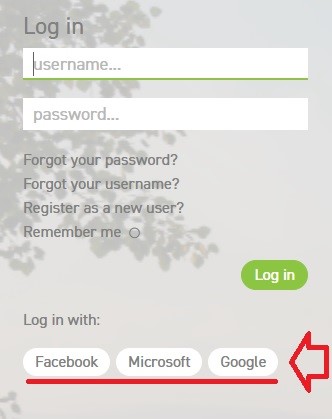
This is a form of Single Sign-on.
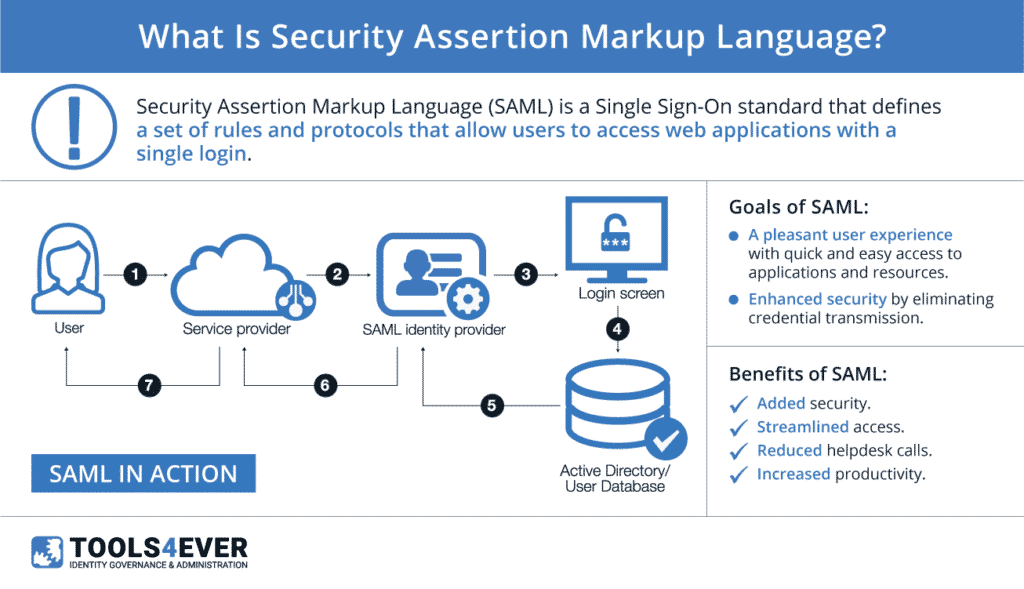
The service provider trusts the from the identity provider to provide access to its services or resources.


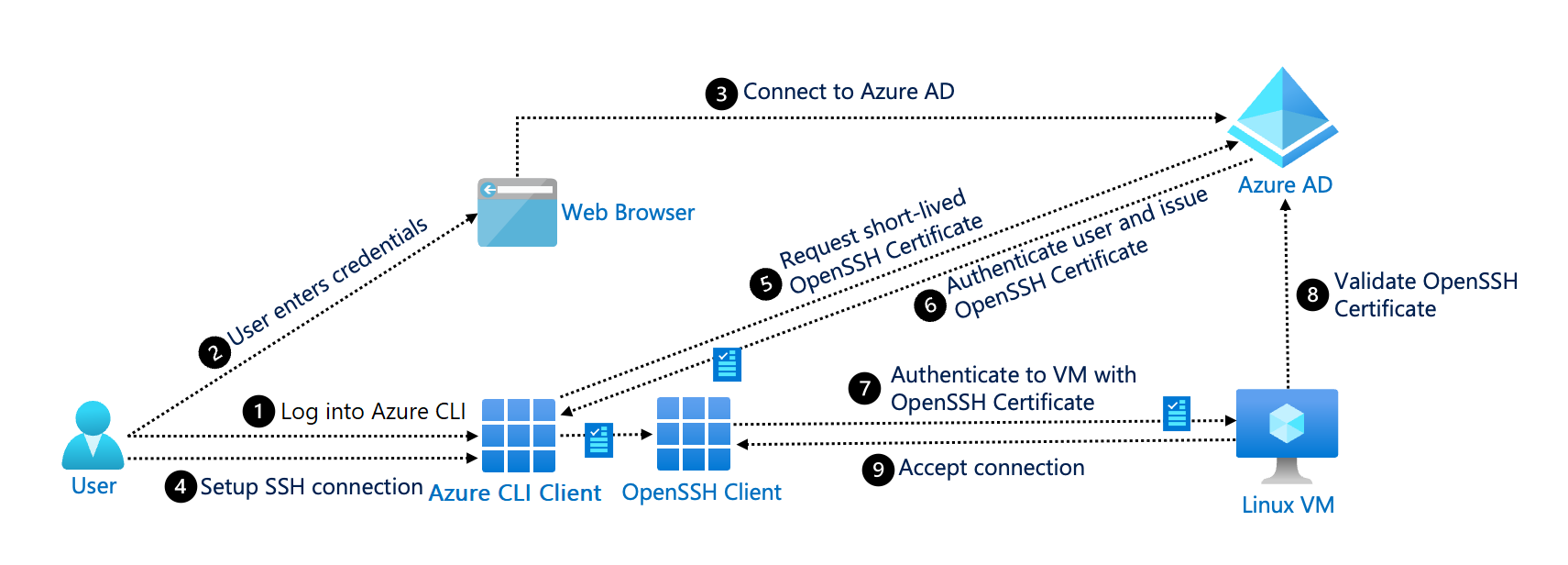

Description: For an in-depth technical discussion of this transition, see.
Sexy:
Funny:
Views: 7957
Date: 27.03.2022
Favorited: 165

Category: DEFAULT
User Comments 3
More Photos
Latest Photos
Latest Comments
- +391reps
- By using this system, the user consents to such access, reading, interception, monitoring, recording, copying, audit, inspection and disclosure for any purpose.
- By: Tenney
- +946reps
- Individuals accessing or attempting to gain unauthorized access to this system will be prosecuted to the full extent of all applicable laws.
- By: Deborath
- +746reps
- Message and data rates may apply.
- By: Adina
- +588reps
- A solution suggests that there is the ability to expand or customize the capabilities of the core product.
- By: Banwell
- +54reps
- As different applications and resources support different mechanisms, single sign-on must internally store the credentials used for initial authentication and translate them to the credentials required for the different mechanisms.
- By: Pistol
sexyass.pages.dev - 2022
DISCLAIMER: All models on sexyass.pages.dev adult site are 18 years or older. sexyass.pages.dev has a zero-tolerance policy against ILLEGAL pornography. All galleries and links are provided by 3rd parties. We have no control over the content of these pages. We take no responsibility for the content on any website which we link to, please use your own discretion while surfing the porn links.
Contact us | Privacy Policy | 18 USC 2257 | DMCA
DISCLAIMER: All models on sexyass.pages.dev adult site are 18 years or older. sexyass.pages.dev has a zero-tolerance policy against ILLEGAL pornography. All galleries and links are provided by 3rd parties. We have no control over the content of these pages. We take no responsibility for the content on any website which we link to, please use your own discretion while surfing the porn links.
Contact us | Privacy Policy | 18 USC 2257 | DMCA



































